Three Business Models
- Innovation to Invent
- Change to Improve
- Operate to run the business
Sub-Account Code
- 30 Innovation
- 20 Change
- 10 Run
Risk Management
- High Risk – innovation
- Medium Risk – change
- Low Risk – run
The real world assumes fact based sources and actual dimensions for example zip codes are fact based and actual dimensions are related to the zip code.
If we acquire information from the Census Buruea we have acquired “facts”. If we acquire information from a report, we are acquiring a sponsored report which will reflect the views of the person sponsoring the report. Certainly some reports are derived by people who intend to acquire facts, although the scope and facts are limited to the views and understanding of the people performing the work.
The report sponsored by anyone whether private or public sector and regardless of the people performing the work, the results must be assumed as “Fit for Purpose”. The world has taken on this assumption about the viability of a any successful company as an example; people believe the company requires fit for purpose above the Real World in all scenarios.
However, we know that most companies are in silo’s and this introduces significant waste in an organization. Therefore, fit for purpose is not the best approach it is an acceptable approach if the business and management systems are tightly integrated away from fit for purpose layer.
These two terms were introduced to me by an expert blogger Jim Harris via a Radio Show he hosted with a guest speaker who framed the conversation in the same way with different examples.
Let’s consider the external stakeholders, shareholders, investors and regulatory requirements for any company would need to be working by Real World definitions. We might have very strategic ways of supplying both with little disruption in most cases.
The approach would restore systems with leverage points and feedback looks at the places where both suppliers and customers interact with an organization and employees in ways that could be determined by each company, knowing these are vital to the companies quality management systems.
Enabling discreet monitoring and fact based decision making using the highway analogy.
Assume that Wisdom as a Service offers the client just what I am describing beginning with a baseline assessment of the organization as it today and what we measure as a standard. The standard is the basis for Real World when applied to your organization.
Wisdom as a Service
A service offer which enables the effort to attain your priority 1 “lights on” scope based on regulatory and financial accountability. Yes, WaaS intends to minimize your risk and limit governance to a core smanner (typically ERP). Enabling all inputs to push from other functional applications which arrive in a manner which
Wicked Design Solutions
Lisa Martinez 408.577.7130
Belonging to a certain general class (genus). Also, an item not marketed with a brand name, trademark, or other distinguishing feature that separates it from other similar items.
Read more: http://www.businessdictionary.com/definition/generic.html#ixzz2kCb48Q9k
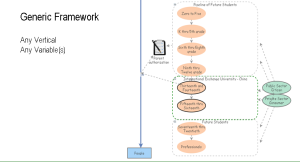
A common measurement which would be true for any population. A group of people in a GIS code infers a true measure for people all over the world. A vector would be set and true for all variables when applied in a model. The population volume remains x when a modeler applies “A Variable” to the population. A modeler doesn’t not want to add the population as a variable otherwise the model simulation will work as effectively.
A model which can be used by any vertical market. Notice the segmentation of a population grouping children by milestones. Different variables apply to each of these populations. The child populations are shown with a parent authorization true for each person in the segment. The concept applies a filter type concept which requires a parent to have visibility and apply an authorization to use any online service.
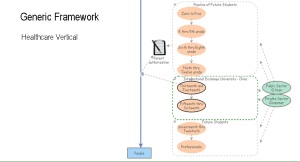
A model which would be applicable to the healthcare industry variables.
A set of variables “true” in the education vertical.
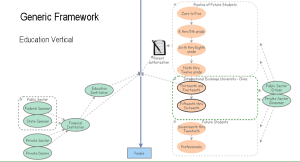
A media and entertainment model applied to the education model.
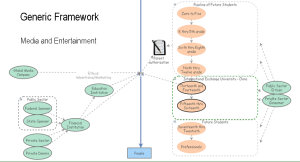
The above definition must be assumed for any online protection framework. Online protection for children or victims of violence have a reasonable expectation of privacy and advertising in no way justifies any reasonable expectation other than these populations have additional safeguards and greater risk of harm to physical safety.
An open standard solution currently being developed as a viable option for parental authorization and a reasonable expectation of privacy.
The following diagram infers the way information would ideally remain unique to 3rd party applications and Platform Providers when a per cloud user acquires an application from the Play Store or iTunes.
The change required for 3rd party applications and Service Providers would be to refrain from all restricted data types and only acquire “Selected Visible”. The change supports the many laws in place which protect people from others collecting or reselling for any reason.
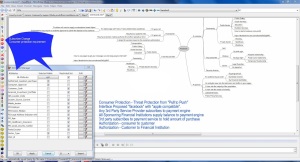
Mobility services need to be revisited and controls put in place at the release of applications into the mainstream through these two stores primarily. An assumption is made that Google and Apple are managing their stores with integrity. Therefore, understanding and changing the way these applications can damage an asset or use up the data minutes inadvertantly for users. Well this is a responsibility for these two providers who host the stores where people acquire these applications.
Understanding the general systems theory and application of the generic process framework which is a sub-system and constraint for all systems.
Step 1 Business Process 1 – Design the Strategy and Vision for an offer.
The management decision making process which must occur and iterates each year or in investment firms in the financial market would be the only example where this process may occur more often. This is true for the fact that all planning follows one of three paths.
In today’s world we believe we are running with these basic concepts in our tools and process. In our process and our people practice or seek the ability to either run the business in operations of the enterprise. Change the business in continous improvement of the business operations of the enterprise. When we innovate we are transforming a market and therefore need to remain in the Portfolio layer of the enterprise.
We must assume the fact that a project manager is not going to qualify as a program manager, to manage the program with more than 1 project a person must invest in thier professional development through the enterprise employee development process or as a personal investment. In order to move into the portfolio part of a business we must invest in program level or advanced certification and then work towards an expert certification as a portfolio manager. In any enterprise the rule can apply to all resource in the Enterprise.
A portfolio must be managed by the Expert in a market offer lets apply the concept of education as the portfolio and we can assume this has a relationship with children who receive education, parents who make decisions and are the primary customer in the education industry, teachers who provide a service and the federal government supplies the majority of the funds to a delivery system which includes the state departments, county offices, local districts and schools.
The point of interest being the students are not the primary decision maker the parent is the customer in education. We learn from the moment we can feel and hear in our mothers womb, but we start the social system at birth. We know we have Federal Sponsors of the majority of our education dollars What if our deficit problem was a direct result of not educating people and not understanding the relationships in a system.
We learn in both public and private life, our economic life determines the quality and whether we can apply the learning more broadly to improve our social and family life or protect our health and physical safety by increasing our economic life opportunities.
acquire approval for operational, continuous improvement or change cost for all branches in government and all organizations or agencies.
Step 2 – begin cost estimates
Benefits framework for all cost intended to benefit citizens
Step 1 – Identify the benefits audience for operational cost for all branches to the citizen or consumer
Step 2 – identify the benefits audience and method of delivery for all future branch cost
A nationwide movement has formed dedicated to engaging those left behind towards computer science. A wicked solution to a wicked problem in our country, mass populations without jobs, without hope and destined for low wage jobs. A country without the domestic workforce seeking talent from under-developed countries where the skilled workforce is exceeding our countries ability to compete.
Solution Life cycle
The business model by customer audience versus unique organization or agency approaches – it is absurd to expect different results using the same approaches.
A social media strategy for cloud adoption “as citizens”
A social media strategy for “any size organization or agency”.
A social media strategy for “any government”.
A community support model explained
Just as we experience with any new innovation offer we must perform due diligence on any proposed supplier. The innovation business model has the highest probability of a new relationship with a new supplier. It is vitally important to manage confidentiality and intellectual property with Non-Disclosure agreements and secure process measurements.
Using consistent supply chain due diligence practices to begin on-boarding of any new suppliers. In the innovation space the intellectual property threats and strong oversight of the supplier relationship is vital to all interactions throughout the first year and longer in cases where solutions are systems or solutions versus boxes.
scorecards tailored to a new supplier who’s value proposition would be measured by quality rather than quantity. Ensuring a build order transfer model or twice removed model in small and medium customer scenarios requires a very strong negotiation team and consistent communications amongst the internal team especially in front of the supplier.
Very smart people “who simply are motivated by mass processing” “the bigger the greater the accomplishment or assumption of meeting a higher level of expertise”. Very smart people in business roles are still scratching their heads about how the audits continue to imply workarounds are being allowed in controlled applications.
The problem is conflicting objectives and motivations without accountable leaders to manage the corporate policies within an organization.
The limitations with this audience relates to the non-technical outcomes caused by big data concepts.
I am much more the resource from the following roles;
If the above is true, who has commissioned the tons of data and for what purpose?
What does it mean when a data expert does a data type change or creates a new physical table?
Changing a report, connecting or changing the source data in order to present insights has the greatest threat of being misused by the sponsoring business stakeholder. Far too often the business stakeholder is actually an IT team within a business unit who’s implementation failed adoption or was incorrectly implemented (irregardless of who failed) and the fastest way to mask the problem is to produce insights that say the implementation went well and nothings changed.
When an organization or agency plans a purchase of software from a 3rd party or an external software company as an example in transforming to cloud solutions, the purchase either includes a one time fee;
In the case of a cloud solution, the annual maintenance should cover all normal events. If you find your organization being asked to pay for cost or hearing “performance issues” or customizations that prevent your organization from introducing updates on a regular basis. These are all symptoms of an operational, quality and governance situation.
In some situations;
Your 3rd party software provider – has a list of exclusions and charges added fees due to implementation decisions
If you were supplied a proposal to purchase software for a business unit, you must ask questions about the return on investment or total cost of ownership. Far too often business people assume software solves people, process or technology problems without performing the appropriate process benchmarking exercise with people who are unbiased. People who are not going to be politically motivated, not to say these resources would not be sensitive to the stakeholder political points of influence, the most qualified resources being outsourced to an organization specializing in Benchmarking or a mature organizations Business Architect leading with Enterprise Architect validating.
Having an inventory of the capabilities and tools purchased with the same capabilities isn’t unusual, not all software tools are known for or specialize in all capabilities instead the vendors design a solution that a company can buy and use without any integration to meet small and medium customers needs and the large global customers need to rely on their IT Architecture teams and data architects to redirect the software to the source based on policy and procedures defined at the corporate policy level.
Every software package I’ve evaluated in the past 20 years, has the ability to create a customer.
A party management capability ensures the appropriate controls are designed into an architecture with a segregation of duties by design. The create, read, update and archive must be honored and monitored or proven to annual audit stakeholders and may force an organization to restate their performance in cases where an organization or agency fails to manage the due diligence scope prescribed in General Accounting Acceptable Principles. Non-GAAP revenue outside the innovation or advanced technology risk typically reported in a footnote or excluded from GAAP performance.
If an Enterprise and Business Architecture team isn’t an invested resource supporting the organization or agency or if these resources are unaware of the risk and severity. We have a large audience who’s perfectly aligned to their culture and the unfortunate risk for the company happens to be a WICKED problem.
The organization has operational waste that may has a high probability to impact both top and bottom line financial impacts, considering the stakeholders in an operational waste situation the probability is high for threats to reputation, competition and regulatory risk.
Physical Security – Executive Officers 404 assurances-The part of the risk that D&O insurance cannot cover for any executive officer.
In fairness, the above would be the worst case scenario and it certainly isn’t politically correct to take this to your executives.
Imagine being in a role where the executive hands you a stack of papers and wants to know why the organization has more than 300 applications charged by IT each quarter?
If you are in charge of tools and just walked in after implementation of a host of new 3rd party applications were launched and users refuse to use the new investments.
Well, imagine you retire or submit the retirement plan and move to a new role where you can ensure and influence the retirement of the legacy out of scope or shadow applications. What if you are unaware the new team you joined actually happens to be the reason these applications are being charged to your former group?
We must acknowledge resource motivations and respond with a solution that contains the threats to an organization.
I can agree only in situations where party, offer and financial account codes are not included in the scope.
The analytical component changes to a transactional shadow application when “get” or “create” commands are in the code.
What if those applications are only considered an application because of a transformation done outside the system of record.
Unfortunately, Big Data has proven to include the above behaviors
How to identify if your organization has assumed a risk by investing in Big Data?
If your organization happens to be investing in and promoting Big Data; especially following a security and resilience transformation you may have not gained the benefits you intended.
You are unlikely to be positioned well for the cyber=security requirements and need to spend some time understanding the severity of risk with a discreet assessment.
If your organization hasn’t defined the priority zero data loss and zero downtime scope or you have more than 15 applications in this class of your resilience response testing each release, I’d suggest a discreet security assessment.
The ability to create master records, with the Enterprise Resource Planning, Opportunity Management, Application Tracking System, CMBD, Extranet/Intranet, Records Management, Project Accounting, Supply Chain and Service Management Modules.
These transactions are the leverage points for most privacy, compliance, and security classification with highest protection or need to know only.
The threats for these transactions are always going to have the highest probability for all four security principle risk types in any organization or agency;
In cases of any of the above mentioned gaps in your Enterprise Architecture or hosted solution providers;
- Symptoms include lower quality customer data, as these other application users are being forced to enter a field they are not qualified nor authorized to enter.
- Symptoms include higher number of null values in party tables
- Symptoms include higher number of duplicate indices
- Symptoms include higher pricing disputes
- Symptoms include higher tax issues or disputes
Be cautious when noticing anomolies in the reporting around the subjects, as you will find a report was modified. The changes were unlikely to be put in place.
Instead you are the proud owner of a report that reflects a subjective view of the organizations performance
Don’t be concerned, you are not alone. Many leaders fall for the “we can do that for only a fraction of the cost”, we are agile unlike most of the stakeholders.
To help us understand how many people fell into the same trap, try counting the duplicate indexes or null values in fields like the zip code or state.
Any person, organization or agency should be reviewed in this context. You will find that the largest tables are customers. Now segment the three sub-types.
Assume every table suggests a unique list of customers or a list that has the subjective rules applied by people who build custom shadow analytical solutions.
Let me share the difference between analytical applications and operational applications. Today these lines are blurred. An analytical application is not controlled at the application source; it acquires the information transforms and then reloads.
The primary root cause of data quality failures “the ETL” process and even fewer records are maintained by the developers.
The primary tool used to modify records or connect unconnected data sets happens to be an integration or ETL solution. Curated or processed information being the newest and most relative terms used to articulate offline shadow applications.
These people are doing their work in fire drills and even the best Architects are only as effective as their clients demand them to be. These resources are Miracle workers. The challenge is they are not the right people to solve the problems.
A tool used by any size and across verticals to target an audience for ethical advertising and marketing or transitioning to a digital media focused on a customer centered design.
A media publisher currently uses various methods of deliver and has recently decided to accelerate change by adopting a digital media strategy. Part of the strategy includes selling or segmenting a major part of their organization to one of the current distribution channel strategic alliances. The result will be a billion dollar change to revenue moving the companies direct consumer model to that alliance company. The initial cost and revenue streams will change dramatically, while the outcomes will be far less volatile for future operations.
A challenge imposed on a LinkedIn forum, to prove a common model can be applied to two different size and types of organizations.
The following represents the customer or person centered design strategy which was derived in order to enable a single record for every citizen or a master data design model.
The right side of the stock and flow model provides the static converters about an audience, using the vectors in the tool one must assign the measurements for a region which you intend to simulate.
The left side provides various converters which will change the simulation results when applied to the right side population by variable framework. A one page model to base any strategy regardless of the internal business environment. Each organization will be unique, having a standard way to view a consumer aides in lowering the internal expense we apply trying to figure out the right source for such information. Open Government will align well with this simulation model.
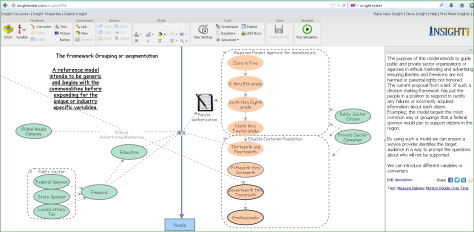
Whenever we approach design we need to understand and observe, we also must measure and prototype. The above is a model within an open source tool used to simulate system architypes or stock and flow models. In this situation the variables we need to understand are static. A human at all points in time has an associated milestone in their mental models or learning workflow. Age and content appropriate materials are vital to the success of a person’s ability to experience change or learn a new lesson in a different or mature in a known subject. Irrespective of the organizations business model or decisions the facts are true and not within the control of any organization or agency alone.
A tool developed by the board of directors to guide the business decisions within the control of the organization. Without a framework to prevent decisions made outside the control of the decision makers, we must supply the boundaries in order to ensure compliance and adherence to the corporate policies.
In order to attain the validity and integrity of an audience we must understand these known facts about the audience. For this reason we can assume a consumer or a citizen has no customer relationship until an exchange of goods or services is planned and two legal entities enter into an agreement in exchange for commerce. The route to market is a different business model conversation. As stated and agreed broadly, a business model changes when strategy dictates the change. This framework is a static tool designed for dynamic application using common facts or known scenarios outside the control of any organization or agencies ability to influence.
The legal liabilities and skills required to prevent these risk are not typically a core competency recruiters would identify as within the culture of many large corporations. In fact, a person who had these skills would NOT be a good fit in most recruiters selection process. Therefore, the market has few people with this skill. For this reason, change rarely factors the consumer rights, constitutional rights and liberties where these freedom’s are primary to the way people live. For this reason, the framework offers a tool to interact with open government and allows your organization to accelerate adoption of a digital media strategy.
Any organization or agency can ensure high performing systems in any application whether consumer or citizen.
Any organization or agency can collect or disseminate the users by these groupings with little effort, using an open government model with open source tools.
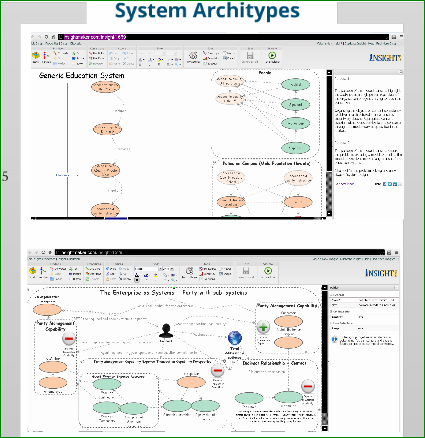
What everyone needs to know about leveraging a digital media strategy for transforming your organization?
To be or not to be is the question! Actually, the question is how does a public or private sector organization address route to market known or things outside any organization or agencies control?
Think Enterprise as a System or social systems. A social system in my mind looks at a person over time, based on milestones for targeting messaging based on ethical advertising and marketing.
Everyone in the world learns throughout life we consume content as information, when organized it becomes knowledge and when we understand and apply the knowledge we gain wisdom. The learning process is a lifelong experience. The framework reminds us and supplies the differences for us systemically.
A social system uses a person centered design strategy.
A person centered design strategy uses social media as a channel!
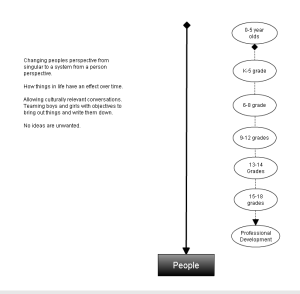
A window into every parent before communicating with the children a parent has in their family. Ideally, a parent can select a milestone group page. 0-5 year olds, K-5the grade, Middle school 6th-8th grade, 9th-12th grade and you can assume two more education levels and the final workforce development.
Imagine if over the period of your life, you experience learning from 100 different sources. Who keeps track of this for you? Maybe you shop at 1,000,000 retail stores, who’s keeping track of this information? I assure you, someone is keeping track it’s just not being done very well. Hence, the need for Big Data!
If every company and every agency creates a customer record for every person on the planet, we have Big Data. The lean approach to this problem would redesign the way people and the relevant information about people is tracked and applied to a single record for every person.
A person centered design uses the natural flow of information and leverage points to manage feedback loops to connect information to enable high performing systems. Basically, by connecting principles we use the same points to measure each area of focus for reliable, repeatable and information with integrity.
A person who can think like this is much more like a Chief Innovation and Strategy Officer. Just saying. 🙂